
 |
trusting Harry Potterveryard projects > trust > potter |
| on this page | some problems of wizard trust | more pottering |
| The Harry Potter books provide some excellent illustrations of some important issues in relation to Trust and Security. | Trusting in Appearance
Wizards are vulnerable to the tricks of other wizards, and so place their
trust in unreliable things - people, artefacts, evidence.
Context-Dependent Trust Can we trust Professor Lupin with the care of our children? Not when there's a full moon ... Networks of Trust Who betrayed Harry Potter's parents |
Muggle Ontology |
 |
Trusting in Appearanceveryard projects > trust > potter > appearance |
One of the things I find surprising is the fact that wizards are regularly
fooled by the tricks of other wizards, and so place their trust in unreliable
things - people, artefacts, evidence. One wonders how the Ministry of Magic
is able to perform any useful function at all, if it is systematically
unable to detect these tricks.
| PolyJuice
Potion |
This magical potion apparently enables one wizard to impersonate another. In the Goblet of Fire, even Dumbledore is fooled. | |
| Time
Turner |
This allows a wizard to be in two places at once. In the Prisoner of
Azkaban, Harry and Hermione use this to frustrate the plans of the Ministry
of Magic, while retaining a cast-iron alibi.
Interestingly, Hermione's possession of the Time Turner had previously been authorized by the Ministry of Magic - presumably by a separate department. Clearly the wizarding world has failed to embrace Joined-Up-Government. |
|
| Memory
Modification |
In the Order of the Phoenix, a quick-witted wizard alters the memory of a witness, to avoid a potentially dangerous disclosure. | |
| Quidditch | The opportunities for cheating at Quidditch seem endless. For example,
there are several instances in the book where key artefacts (brooms, bludgers)
are jinxed by watching stakeholders.
(In contrast, some of the cheating that goes on around the Triwizard Tournament seems touchingly naive.) |
Of course, in the Muggle world, there are no such tricks. Therefore we can always place perfect trust in our sense of What Is Going On.
 |
Context-Dependent Trustveryard projects > trust > potter > context |
Remus Lupin has two identities - man and werwolf. As man, he is an excellent teacher. As werwolf he is a danger to himself and others. However, the werwolf identity manifests itself only at the full moon; at other times Lupin is perfectly safe.
It is not unusual for decisions of trust to make a distinction between different identities of the same person. Let's say I have a friend called John. John-sober and John-drunk are two different identities, with recognizably different patterns of behaviour and risk. I am happy to lend my car keys to John-sober, but not to John-drunk.
If a person has a gun to his head, or his children are held hostage, his behaviour is likely to be uncharacteristic. ("You are not yourself today.") Signatures and voice patterns change under stressful conditions, including duress and torture. If this uncharacteristic behaviour is detected at a security checkpoint, then it might be appropriate to hinder his entry, until the identity difference is resolved.
This is about a difference in identity, not just a difference in behaviour.
I am not refusing John my car keys because of his slurred speech; I am
refusing them because he is drunk It may be his slurred speech that
alerts me to the fact that he is drunk; but if he convinces me that his
slurred speech on this occasion is a result of a visit to the dentist,
I may let him have the car keys. Conversely, if he learns to speak normally
even when drunk, I shall just have to find a different way to determine
when he is drunk and when sober.
| Differentiated Identity |
 |
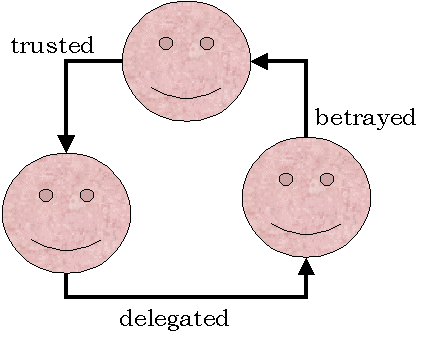
Networks of Trust - Who Betrayed Harry Potter's Parents?veryard projects > trust > potter > networks of trust |
| The best-selling children’s novel, Harry Potter and the Prisoner
of Azkaban, illustrates several important points about trust. Harry’s
parents are hiding from the Dark Lord ("He Who Must Not Be Named"). James
Potter can nominate one friend to guard the secret of his whereabouts,
and chooses his strongest and apparently most trustworthy friend – Sirius
Black. But for Sirius, being the obvious choice makes him immediately vulnerable
to attack: in systems engineering terms, he is a single point of failure.
He decides that the Potters’ secret would be better guarded by a less obvious
person, and delegates the responsibility to a weaker wizard – Peter Pettigrew
– who immediately betrays the Potters.
This is an example of transitive betrayal. It illustrates the following points: |
 |
| The strongest component is the most obvious place to attack – and this makes it vulnerable. A powerful adversary trying to break the system, or to breach its security, may well think it worth investing effort into finding how to break the strongest component. (The system is as weak as its strongest link.) | |
| This leads to the Decoy pattern. A highly visible component draws fire, but isn’t really worth attacking. This is like sending an armoured truck out of the front gate containing the sandwiches, while the gold bullion slips quietly out of the back gate in an unmarked, unarmed van. (The system is stronger than its strongest visible link.) | |
| However, the Decoy pattern is worthless once the illusion is broken. Strength that depends on secrecy is always vulnerable to leakage. A linear (one-to-one) delegation chain is as strong as its weakest link. | |
| To delegate responsibility to weaker components, we need to use the Distributed Delegation pattern – where the system now relies on the concerted strength of all the components working together, rather than being vulnerable to the weakness of each. Parallel (one-to-many) delegation is much stronger than linear delegation. | |
| Trust is transitive – whether you like it or not. If you trust a component from company X, and this depends on a component or service from company Y, then you are implicitly trusting company Y as well, although you may not even know that company Y exists. |
| This is an extract from an article in the April 2001 issue of Interact. For the full article, plus relevant patterns and discussion forum. please register at the CBDi Forum website (Silver/Gold membership required for access to articles, but free Bronze membership will give you access to lots of other resources, including the pattern catalog). | |
| trusting components factsheet (pdf) |
 |
veryard projects > trust > potter |
Copyright © 2003-4 Veryard Projects Ltd http://www.veryard.com/trust/potter.htm |